- 899shares
- Share
- Tweet
- Facebook Messenger
The smartphone you bought is not yours at all.
Every time you accept terms and conditions of a not-so-well-known app, you are indirectly giving the app a permission to do stuff to your phone that you wouldn’t do in your kinkiest dreams.
Smartphones are not secure at all. Add to this the ignorance people carry about the workings of a smartphone and the lack of awareness about the technology itself.
There are many innovative ways your smartphone can be compromised.
1. Phone’s tilt sensor can be used to know what you are typing

Your phone’s accelerometer can predict what keys you are typing on your computer keyboard depending on the distance between the phone and the key being pressed.
This requires the phone to be set close to the computer keyboard you are typing.
Also, the malware can be hidden inside one a very legitimate app and it can figure out what you are typing on your keyboard easily.
Although the accuracy is somewhere between 80%, the hackers are working to make the algorithms more efficient.
2. Special text messages are sent to your phone that can control it completely

When you get a text message, you hear a ping, then vibration, and then a preview on the lock screen.
What if there was none of this, and also there wasn’t any text inside your SMS inbox. Such messages are sent by intelligence agencies to hack into your phone with a piece of software that can activate itself without you pressing any button on the screen.
Once activated the malware takes information from the phone – it could be documents, images or voice recordings.
3. Your debit and credit card info can be stolen by just keeping them around

Are you one of those people with the snazzy credit card that you do not have to swipe in those stupid machines. You just wave it in front of a scanner and that’s it?
And if you are not living under a rock, you must have noticed that the new smartphones are NFC enabled.
That is all you need – a hacker with a modified smartphone with an NFC chip, and you standing in his proximity with your brand new card in your pocket.
4. Hackers can piggyback into open wifi networks and do illegal things
Your friend’s internet pack got over and he is mooching off your internet using your phone’s hotspot?
If it is for only a few minutes, and you haven’t set a password, because it is too much work, you may be putting your phone security at risk. Hackers can use your unsecured network to do illegal activities that can trace the crime to your phone.
5. Free charging stations can steal all your phone data

If you cannot see a phone charger, do not plug your phone for charging into one of these – even if your phone battery is about to die. Behind the charging panel might be a computer that is mining all the data in your phone.
How?
Because the slot for data exchange and phone charging is the same. These hackers can steal all your saved passwords and by extension, have access to all your accounts, and then steal the information from there.
But all your accounts are linked to your phone as an additional security measure, right?
They will put in a malware that accepts all the security requests your phone gets, while you were charging your phone.
6. Some malware also kidnap your phone
Ransomware became a known word when it hit personal computers, but smartphone attacks were unknown – until 2014 when a ransomware hit Android phones, demanding money because the software claimed that your phone has child pornography.
People paid out of panic because they almost believed the hoax.
7. Almost all flashlight apps are full of malware

Have you ever wondered why flashlight apps have privacy policies and suspicious terms and conditions?
That’s because they spy on you.
The least they can do is see what you browse and sell that information to advertisers.
8. Phones can also be used as a listening device

Let’s assume that your phone is watertight in terms of security. You take all the precautions and don’t plug it into anything except your own safe and secure computer.
How then can your phone be hacked?
Hackers can use a device that will act as a cell phone tower so that your smartphone will think that it is connecting to an actual cell phone tower. That’s when the hackers remotely control your phone’s radio chip.
And that means the microphone and all the intimate calls you might be having in your life.
9. Your phone camera can be used to snap pictures when you are not looking

A team of budding hackers built an app that looked legit, but clicked pictures of the phone owner’s home without their permission.
Then all the photos were sent to a server where the images were integrated into a marvelous 3D image of your home – the kind you see when you are house hunting and browsing real estate websites.
The experiment was a success and threw light over the fact that a simple app can compromise your phone and your personal living space so easily.
10. They can control your home appliances with your smartphone
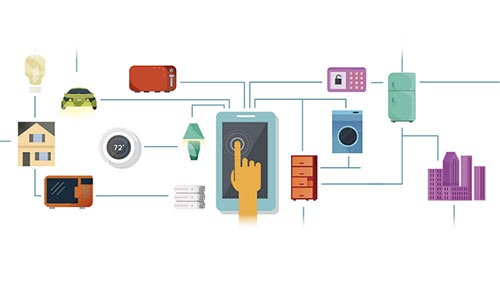
Smart homes are the future. Home appliances are being launched with smartphone apps so smart that you can control your washing machine spin cycle sitting in your office.
Slowly all the appliances are going to fall in this category, and if we take a step forward, even the home security systems – which were hardware based for some time now, but are becoming software-based quickly.
Imagine a crook who has access to the password to enter your house, and by extension can just waltz into the kitchen and fix himself a nutritious glass of juice.
Just saying.
- 899shares
- Share
- Tweet
- Facebook Messenger