- 23.9Kshares
- Share
- Tweet
- Facebook Messenger
This isn’t a story of a random youngster exploiting a bug to his advantage.
This is the exciting (yet a little disappointing. We will get into that in a bit.) story of how a responsible hacker broke into numerous websites, detected security vulnerabilities and instead of using them for his own benefit, reported them to the respective companies.
It’s a little disappointing because almost none of them (except Air India) rewarded him with respect, recognition or money.
One such ethical hacker is this “20 something”, Kanishk Sajnani. He’s hacked into many portals, discovered countless bugs in the security systems and ethically informed the concerned websites about it.

Sharing his experience on Medium, Kanishk penned down anecdotes from his hacking history that involves hacking Air India, SpiceJet, Cleartrip and more than a few other Indian websites. In his own words, he did that all in a month.
“I never shared any of my findings with anyone else. I’m doing it now because their applications have been updated & thus bugs have been removed.”
In a very detailed first person account, Sajnani revealed how he managed to book a flight to San Francisco for just Re 1, booked another flight for Rs 4 and got a refund of Rs 2000, booked a free Spa and got a refund of Rs 1199 and his tale of free biryanis, too.
In 2015, he found a bug in the Air India portal and booked himself a seat on a US-bound flight for just Re 1. Yep! He could’ve travelled the world for free. But did he do that? Nope! Instead, he wrote them an email (on November 4, 2015), informing them about the bug. But a call was waiting for him.
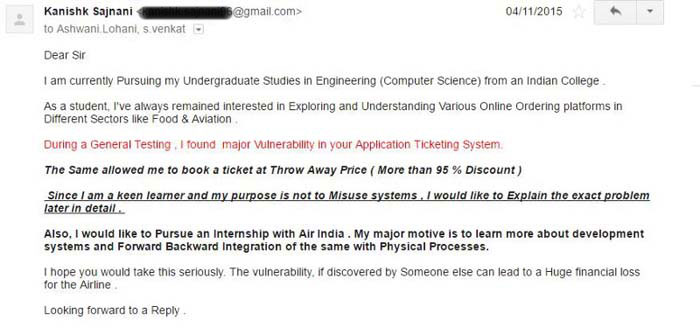
“Received an unexpected phone call from their Manager(Finance) on 12th Nov 15′. He asked me to prove if such a vulnerability existed & Oh boy! Did I?”
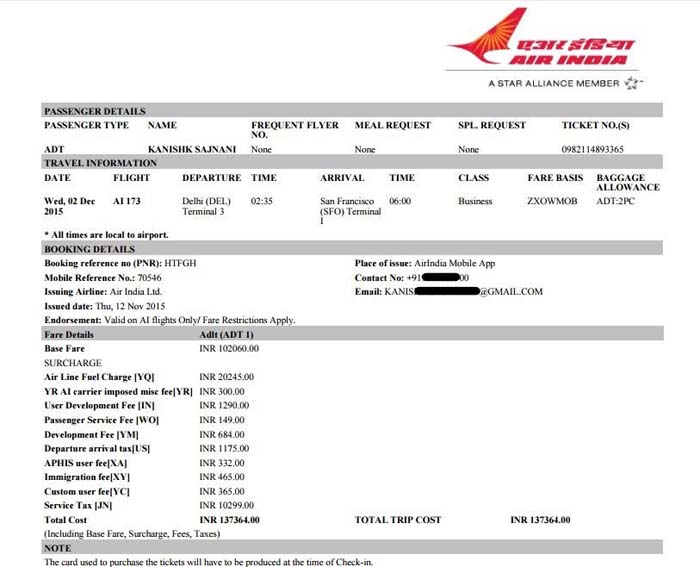
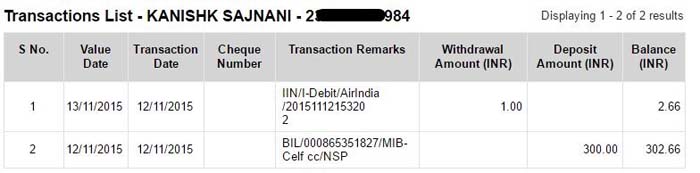
The details were legit and the manager asked him about the rectification measures, for which he sent the details (POC- Proof of Concept) via email. They did offer him an internship, but he didn’t take it up.
Then, comes the tale of SpiceJet. He found a “similar vulnerability in SpiceJet’s Mobile application” and informed them. On October 28, 2015, Kanishk booked a ticket to Goa from Ahmedabad which was worth Rs 4000, but he actually paid Rs 4 for it.
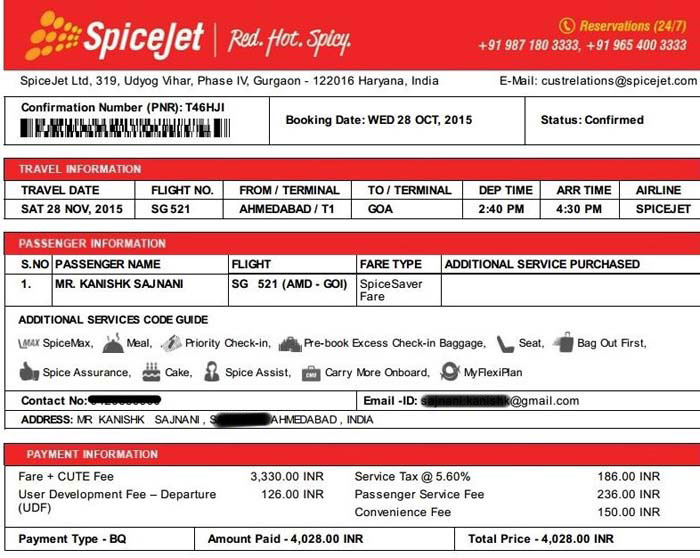
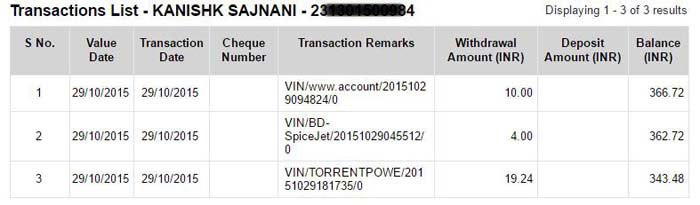
He thought the transaction would get flagged or someone would get in touch with him, but it didn’t happen,
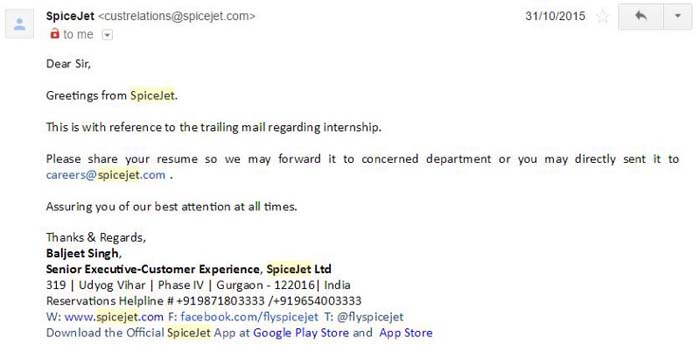
He then reached out to the General Manager, Mr Pradeep Shah (GM, Reservations), who asked him to forward the emails. Which he did, and this was the reply he got.
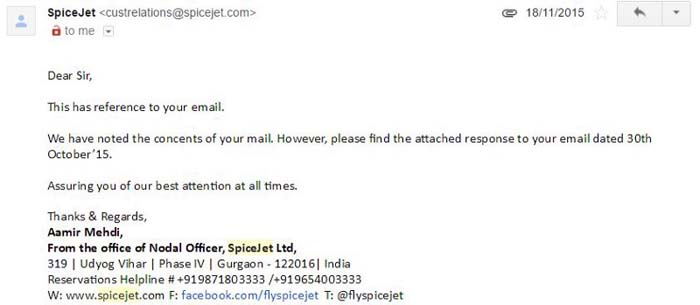
The ticket was valid still but Sajnani cancelled it himself on November 21. The cancellation mail didn’t mention any refund amount. So, he called up the helpline and was told that he was eligible for a refund of Rs 2000, which can be credited to his account or could be used on his next trip. His observation? The financial systems’ back-end couldn’t detect irregularities in payment.
Next was Cleartrip. This was in March 2016. He could’ve “booked flights, hotels, international holidays, trains, restaurant dates, massages, cultural events, sport activities. Anything for absolutely free.” He shared the screenshots in order.
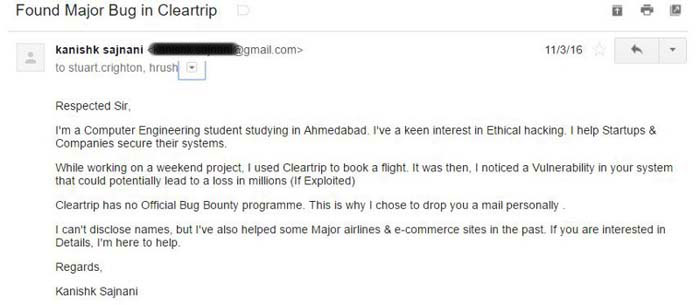
He was asked if that could be discussed over a “quick call”. Kanishk refused it because…
“Never have such conversations over the phone. A written correspondence is must ( You’ll have proof in case something goes wrong) I made an excuse & asked him to continue over here Or on Facebook.”
And, was enticed with a reward-bait.
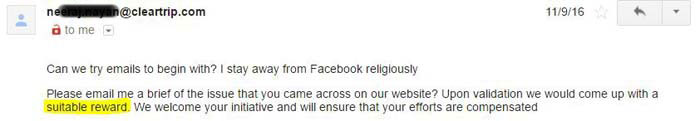
He responded saying,
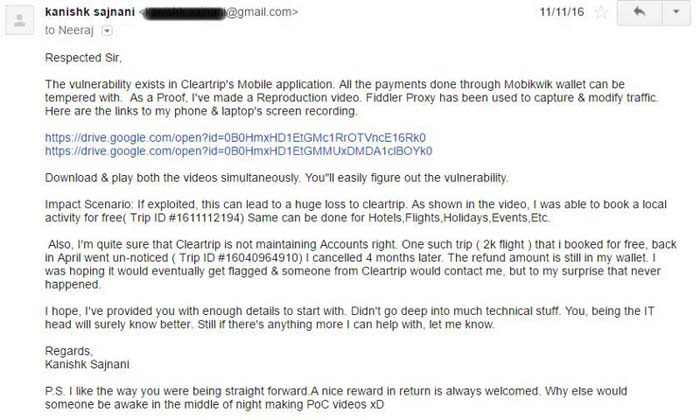
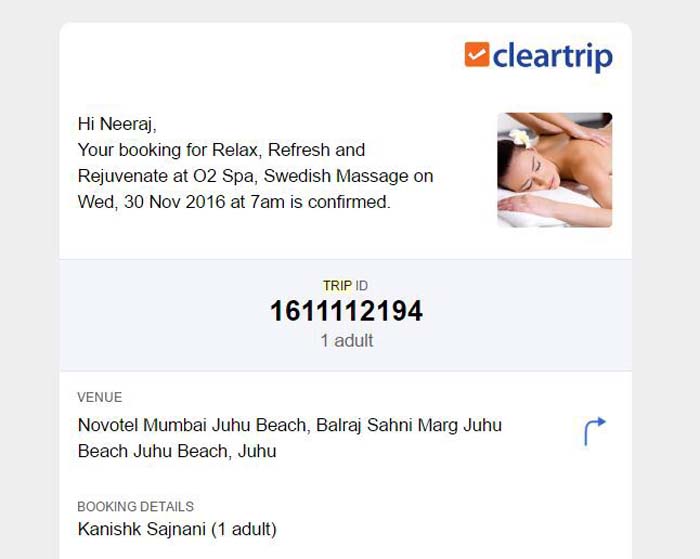
Oh, and then he encountered failed transactions too.
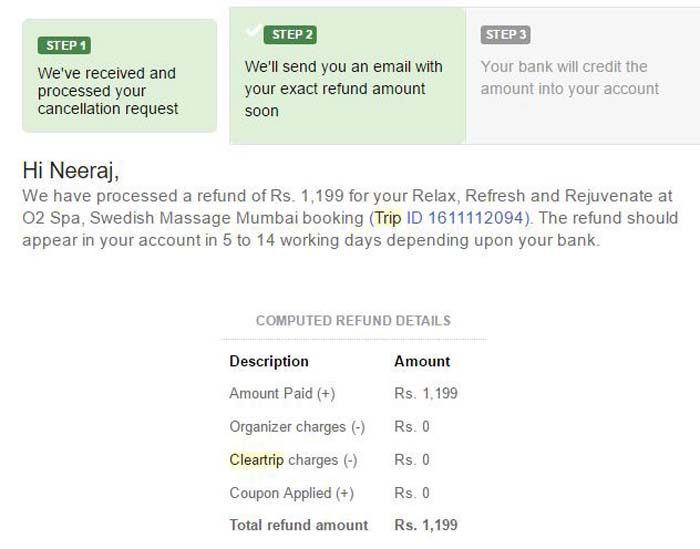
“One of them was automatically processed as ‘Money Paid but failed’. A refund request was generated. My Mobikwik wallet was credited with 1199 Rupees.”
He duly informed them about this too. And, didn’t hear from them again. Next thing he knows, MobiKwik wallet was taken down from their Application and never put back up.
Since he didn’t hear from them again, he shot an email to the co-founders.
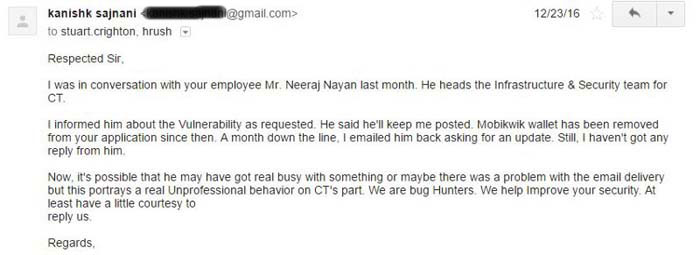
But there was no acknowledgment.
His takeaway?
1. Indian Companies don’t pay the attention required for security of their Products.
2. No Application/Website is entirely secure. Chances are, maybe someone is already exploiting the bugs right under their nose.
3. The only way they understand the Importance of Bug Bounty Programmes is through Public Humiliation. Damage control is obligatory once you get hacked. Best Example – Ola Cabs
4. Ethical Hacking is rarely appreciated.
5. The process of resolution usually takes a lot of time here. I remember submitting a vulnerability to Mobikwik through their Official Programme. I was just able to Brute Force the OTP during Account Creation. They took like five weeks to get it over with & rewarded me with a sum of 2k ₹.
What needs to be changed?
2. Development & Maintenance isn’t everything. The company should be secure from any kind of hacking attempts. Leak of private customer details would mean a massive lawsuit coming your way.
Every Big startup/company should opt for a Bug Bounty Programme Or at least have a Responsible Disclosure Policy. Platforms such as Hackerone Or Bugcrowd can be used too.
3. Appreciate & Acknowledge those who find loopholes in your system.
4. The Cycle of Bug Identification- Resolution- Reward should be as fast as possible.
5. Companies that don’t have their own security Engineers can hire other firms to test their API’s.”
How did it start for him? Faasos’s Application where he could access all the details (Debit card, Addresses, Order History) of any customer just through their email address or Mobile number. And, ordered a few free Biryanis too. No one could notice it, until he came clean and told the delivery boy when he paid in cash, for the first time. And, informed the CEO Mr. Jaydeep Barman. He also had a few emails and call exchanges with his brother (also CTO). The app later got fixed.
He concluded with a summation of his hacking history and a disclosure.
WOW! (Not in a good way, though!) So, is our data really safe?
It was just last week that news of Zomato being hacked made it to the headlines. And, often we keep hearing about the Aadhaar leaks every now and then, or some firm getting hacked.
Kudos to Kanishk and ethical hackers like him who push the envelope of technology to bridge the gap between “what’s safe” and “what’s presumed to be safe”. Companies should be grateful for these extra pairs of vigilant brains that keep their technology stack hacker-proof from prying eyes. Moreover, a bug bounty program won’t really hurt considering the high cost of an invisible and unnoticed vulnerability.
- 23.9Kshares
- Share
- Tweet
- Facebook Messenger